What Is PPP Authentication?
PAP and CHAP
PPP is a data link layer protocol used for establishing a direct connection between two nodes. Authentication in PPP is the process by which the identity of the user or device at one end of the PPP link is verified before granting access to the network.
There are two primary methods of PPP authentication: PAP (Password Authentication Protocol) and CHAP (Challenge Handshake Authentication Protocol).
There are two primary methods of PPP authentication: PAP (Password Authentication Protocol) and CHAP (Challenge Handshake Authentication Protocol).
Password Authentication Protocol (PAP)
PAP is a straightforward method where the user’s identity and password are sent across the network in a clear text format.
While simple, PAP has a security limitation, as the password is transmitted without encryption. This makes it vulnerable to eavesdropping attacks.
Challenge Handshake Authentication Protocol (CHAP)
CHAP is a more secure authentication method compared to PAP. It involves a challenge-response mechanism where the server challenges the client to prove its identity by encrypting a randomly generated challenge with the client’s password.
The client responds with the encrypted challenge, and if the server can decrypt it successfully using the stored password, authentication is successful.
PPP authentication is crucial in ensuring that only authorized users gain access to network resources. It plays a significant role in protecting against unauthorized access and securing sensitive data during the authentication process. The choice between PAP and CHAP depends on the security requirements of the network.
Before Network Layer protocols are allowed to transmit over a link, PPP will spell out an extensible link control protocol that will make room for negotiation of an authentication protocol. This is defined in the RFC 1134.
The authentication phase of a PPP session is optional. If used, you can authenticate the peer after the LCP establishes the link and chooses the authentication protocol. If it is used, authentication takes place before the Network layer protocol configuration phase begins.
The authentication options require that the calling side of the link enter authentication information. This helps to ensure that the user has the permission of the network administrator to make the call. Peer routers exchange authentication messages.
Summary
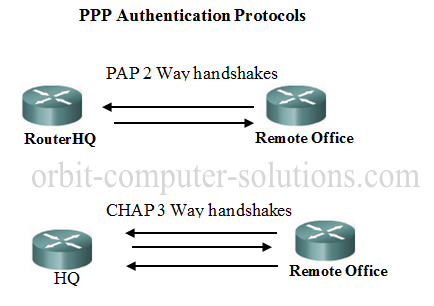
After enabling CHAP or PAP authentication, or both, the local or HQ router requires the remote device to prove its identity before allowing data traffic to flow.
i. PAP authentication requires the remote device to send a username and password to be checked against a matching entry in the local username database or the remote TACACS/TACACS+ database.
ii. CHAP authentication sends a challenge to the remote device. The remote device must encrypt the challenge value with a shared secret and return the encrypted value and its name to the local router in a response message.
The local router uses the name of the remote device to look up the appropriate secret in the local username or remote TACACS/TACACS+ database. It uses the looked-up secret to encrypt the original challenge and verify that the encrypted values match.

